We are proud to announce Threatray Release v2.2. Dive in below to discover its highlights.
Function-level retro-hunting and pivoting is now available in the UI
We are introducing a unique, industry-leading capability to the UI: function-level retro-hunting. When investigating any piece of unknown code, users can now click on unknown functions to trigger a hunt for similar functions within our database of over 1 billion malware and goodware functions (libraries, runtimes, and other legitimate code). The results display all samples containing matching functions, including context and classification where available. The entire process is point-and-click and takes mere seconds.
This capability is essential for quickly uncovering code relationships between seemingly disparate tools, checking the uniqueness of functions for YARA rule creation, and generally for analyzing and pivoting on clusters that share the same function(s).
Operating at the function level allows users to reveal relationships missed by Threatray’s other code pivoting capabilities, which work at the level of files or memory code blocks. It also introduces greater semantic granularity, allowing searches for specific functions like encryption routines, encodings, or communication functions.

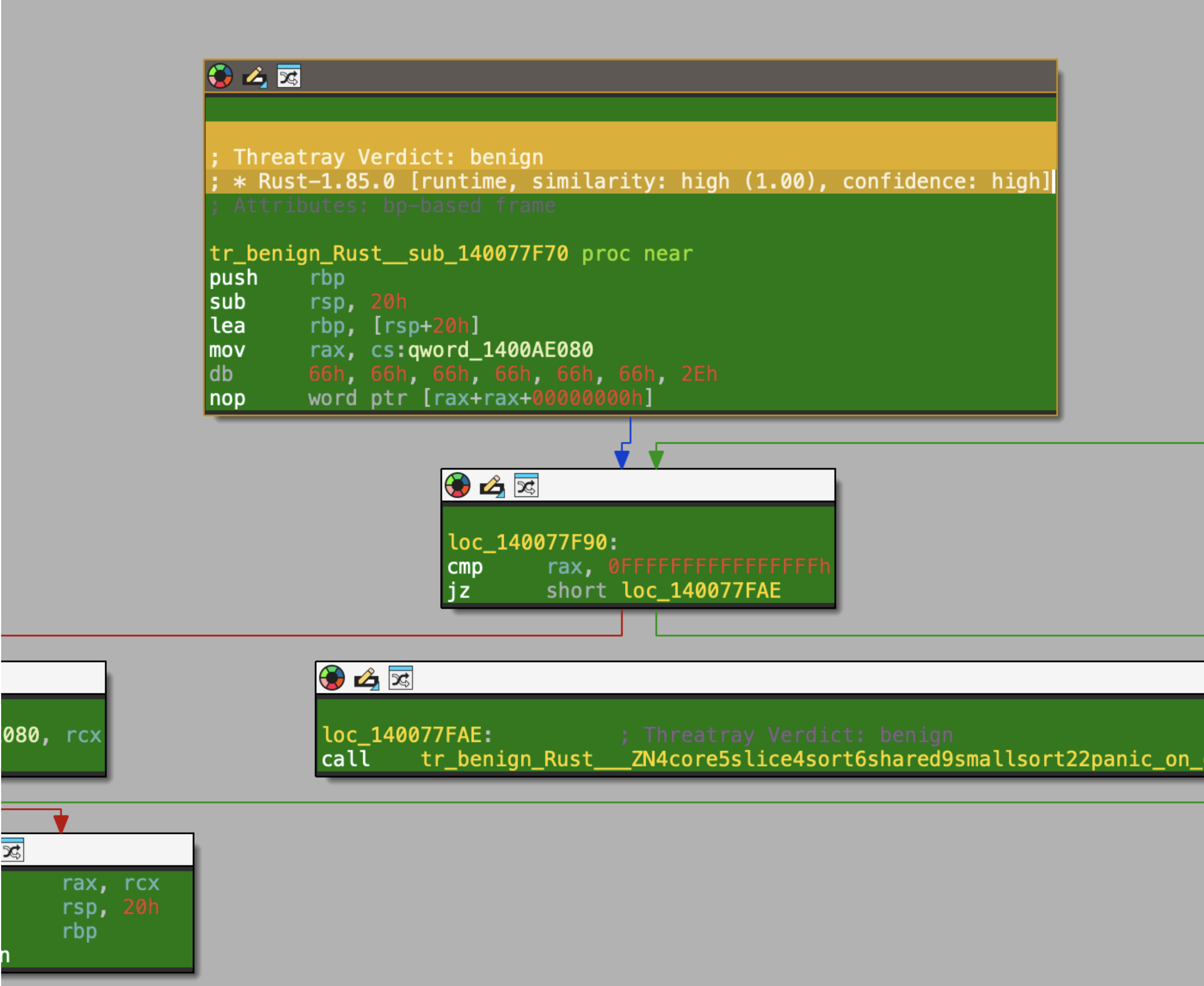
A new version of our Go and Rust Library identification engine
We've rolled out significant improvements to our goodware matching algorithms for Go and Rust binaries, resulting in cleaner and more accurate runtime identification at scale. This is a key capability for users leveraging our IDA Pro plugin or the code intelligence view in the UI, enabling us to rapidly distinguish known good code. We are seeing a boost of up to 40% more goodware function identifications. Furthermore, we have significantly reduced false matches that could occur in certain situations.
We have also made our library attribution more specific, now designating the exact library—for example, "Rust-1.87.0" instead of the generic "benign" used previously.
This improved library identification feature enhances the platform's ability to discern known good code and boosts the accuracy of our code similarity-based malware classification for Go and Rust binaries.
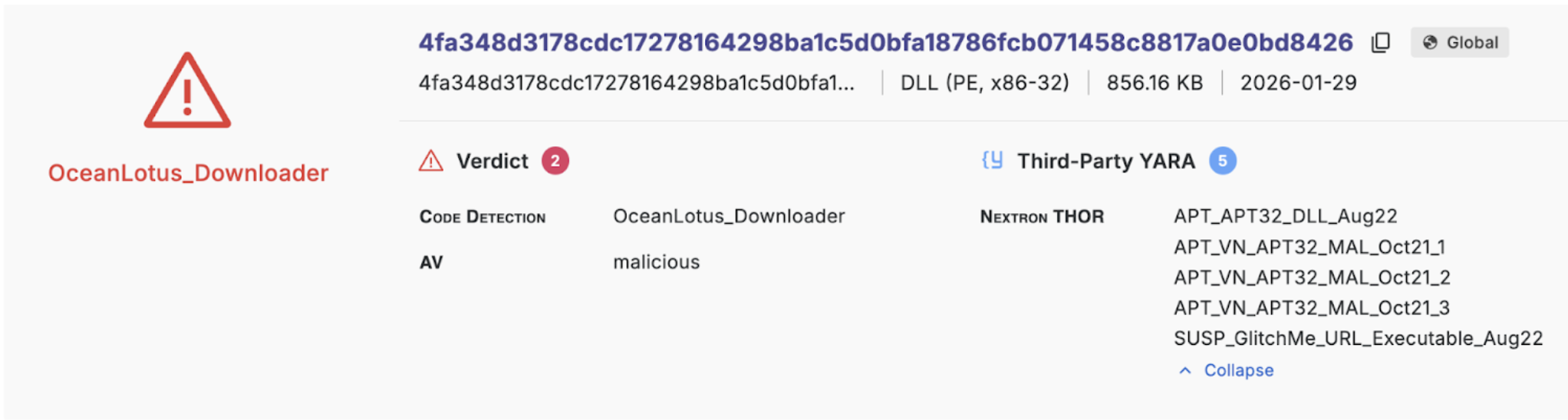
YARA matches now have their own icons for better visibility in the UI
We utilize YARA as a complementary technology for malware classification, alongside our primary and unique code-similarity-based classification engine. We curate open-source YARA rules and also integrate the highly reputed Nextron YARA rule set.
Previously, YARA classification information was occasionally overlooked in the UI. With our new UI release, we've given YARA matches a more prominent visual presence. YARA matches now have their own dedicated icon and are consistently displayed throughout the UI, right alongside our code similarity classifications and detections.
This enhancement allows analysts to quickly grasp all available classification and detection information on the platform, whether it originates from our code similarity engine or from YARA.

.png)


